2024 © TechOnsite All Rights Reserved
Cybersecurity
Dear Business Owner,
Do you have a sneaking suspicion that you current IT guy is not doing everything possible to secure and protect your network?
Home › Cybersecurity


How confident are you that your business could be back up and running fast after a major disaster?


How certain are you that your data is secured from the latest hacker attack, virus or even employee error?


When was the last time you conducted a “test restore” on your data backup to make absolutely sure you could recover your data?


Do you know what you would do if your server was stolen, flooded or destroyed?


Message from the CEO
Hi. My name is J Chun, President of Techonsite Corporation. As a business owner myself, I know how insanely busy you are so I’ll get right to the point of my letter.
Although we have never met, I’d be willing to bet that your computer network – and the critical data it holds – it is not nearly as secure as you think it is. How do I know?
Because over and over again I’m absolutely HORRIFIED by the incompetence and irresponsibility I discover when I audit most business networks. In 98% of the computer networks I review, I find faulty or non-existent backups, security loop holes, shoddy reporting, and flawed systems that simply cost more to maintain and don’t align with the operations of the business.
Although we have never met, I’d be willing to bet that your computer network – and the critical data it holds – it is not nearly as secure as you think it is. How do I know?
Because over and over again I’m absolutely HORRIFIED by the incompetence and irresponsibility I discover when I audit most business networks. In 98% of the computer networks I review, I find faulty or non-existent backups, security loop holes, shoddy reporting, and flawed systems that simply cost more to maintain and don’t align with the operations of the business.
Is your network being supported properly?
If your technician does not score a “yes” on every point, you could be paying for substandard support and
wide open to a very expensive, very frustrating computer disaster:
Responsiveness
Do they answer their phones “live” and respond to support issues in 1 hour or less?
Diligence
Do they insist on monitoring an offsite as well as an onsite backup, or are they letting you rely on outdated tape backups?
Proper Documentation
Have they provided you with written, network documentation detailing what software licenses you have, critical network passwords, and hardware information, or are they the only person with the “keys to the kingdom?”
Meeting Deadlines
Do they complete projects on time and on budget, or does every project end up taking longer and costing more than you expected?
Punctuality
Do they arrive on time and dress professionally?
Comprehensive Invoicing
Do they provide detailed invoices that clearly explain what you are paying for?
Technical Jargons
Do their technicians maintain current vendor certifications and participate in on-going training, or do you feel as though they are learning on your dime?
24/7 Monitoring
Are they remotely monitoring your network 24-7-356 to keep critical security settings, virus definitions and security patches up-to-date?
Periodical Testing
Do they INSIST on doing periodical test restores of your backups to make sure the data is not corrupt and could be restored in the event of a disaster?
Proactive Consulting
Do they consistently (and proactively) offer new ways to improve your network’s performance, or do they wait until you have a problem to make recommendations?
Availability
Do they have other technicians on staff who are familiar with your network in case your regular technician goes on vacation or gets sick?
Guarantee
Do they offer guarantees on their services?
Loyalty
Do they take calls from other clients while working on your network (and on your dime)?
Reliance
Do you have to manage their progress on projects, or do they provide frequent updates, status reports, and follow-up calls and e-mails?
Credibility
Do they offer flat-rate or fixed-fee project quotes, or do they give themselves a wide open playing field with “time and materials?
How It Works
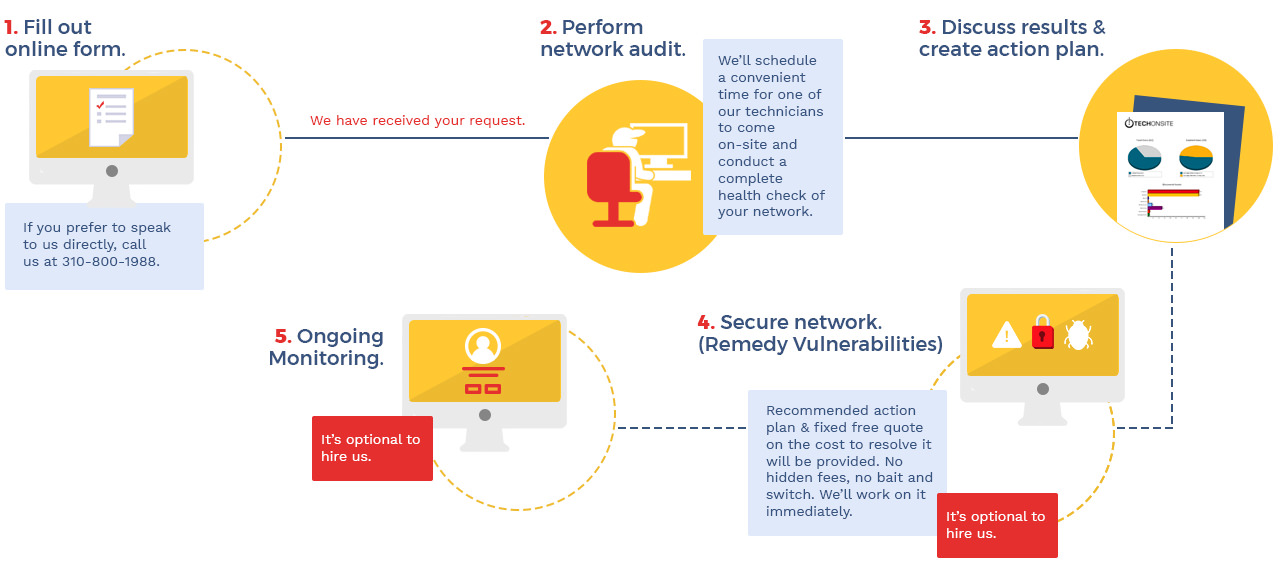



Take the First Step in Securing
Your Network with an Audit
Kindly enter your information below. You must have at least 5 PCs to qualify.

