Not Just For The Kids - Go Back To School
(DON'T STOP LEARNING)
Being a small business owner means wearing many hats, and navigating the path to growth can be overwhelming. One of which is helping your office staff and employees to stay competitive in the workplace, especially in a world where skills need constant updating.
Fortunately, there are several free resources available for remote learning that can help you and your team grow your skills, stay ahead in your careers and accelerate your success without breaking the bank.
There’s also the power of Ai tools that has emerged as a critical component for maintaining competitiveness and driving success. Both business owners and employees must acquire the skills to utilize these resources effectively.
Equipping yourself and your team with artificial intelligence skills will improve not only your business processes but also the assurance of staying ahead in an AI-driven world.
Here are a few key resources that can be invaluable.
(We are not affiliated or endorse any learning platform. They are provided as examples.)
Digital Defense: An Intro to Cybersecurity
Increasing your Cybersecurity knowledge may prevent or mitigate harm to your small business. This beginner course will guide you through identifying common security risks and some initial security measures and best practices.
Leading with Innovation in the Age of Ai
Understand how to accelerate innovation with AI, and how leaders drive innovation. Learn from experts how businesses can change the rules of the game through radical redefinition of the target customer, rethinking the value proposition for the customer, and re-engineering the value chain.
Graphic Design Basics: From The Experts
Learning graphic design can be really rewarding and handy, especially when developing your brand further or improving your brand's visual identity and marketing materials. Learn to create stunning visuals boosting your business's online and offline presence.
Digital Marketing Course
Discover how to create compelling content for users and search engines alike. Gain expertise in diverse digital marketing topics like SEO, social media, email, and more!
Understanding Ai: Introducing Responsible Ai
Learn how to take a responsible approach to AI, built on the foundation of Microsoft's principles, governance system, and processes; and how to responsibly implement generative AI and minimize the risk of generating harmful content.
Time Management: Working From Home
Working from home is a great opportunity, but time management can be really challenging. With so many demands on your time and attention, it is sometimes difficult to be as productive as one would like. Learn how to create your daily schedule for maximum productivity and plan important breaks to avoid burnout.
How to Detect Phishing Scam Emails?
10 Ways to Detect a Phishing Email
Look at the sender’s email address
Ensure the email address is from the correct sender, verify domain and minor character changes, such as "[email protected]" instead of "[email protected]."
Check how you are being addressed
Legitimate companies usually use personalized greetings or address you by your name. Be wary of generic greetings like "Dear Customer" or "Dear User."
Analyze the content and tone of the emai
Phishing emails use urgency and threats to provoke reactions, and abnormal requests for sensitive information, as reputable firms never request such information in emails. For example, "Your account will be suspended" or "Immediate action required."
Check the URLs
Hover over links to display their actual URLs, ensuring they point to the real website. If a link appears to be from "www.bank.com" instead of "www.fakebank.com," it's suspicious.
Analyze the email attachments
Beware of unsolicited attachments, particularly those with .exe, .zip, or .scr file extensions, since these may contain malware.
Go over the grammar and spelling
Phishing emails often contain spelling and grammatical mistakes. Legitimate companies generally do proofreading of their emails for such mistakes.
Verify with the source
If an email appears suspicious, contact the company through their website or customer service number to verify its authenticity.
Use an email filtering solution
Use an email filtering solution to detect and prevent unwanted emails from reaching your inbox using algorithms that immediately place them in quarantine.
Use anti-phishing tools and security software
These are essential tools for detecting and blocking phishing sites in browsers, while comprehensive security software offers real-time protection against malware.
Stay informed and educate yourself
Regularly educate yourself and your team on phisher methodologies and their identification, using resources like mock attacks to raise awareness and build response.
Data Backup
Your first line of defense against cyber threats.
In today’s digital world, cyber threats such as ransomware, malware and data breaches are increasingly common. One of the best ways to protect yourself against these attacks is to have a strong backup system in place.
Having a robust backup strategy prevents ransomware attacks and data loss. Regular backups also ensure business and data continuity, minimizing disruption to business activities during and after a cyberattack, and reducing the impact of human error. Additionally, data backups reduce business risk by providing peace of mind and ensuring critical information is always available when needed.
What are the causes of Data Loss?
Human error
- including accidental deletion and incorrect file handling, is a common cause of data loss, often resulting from users deleting files or format drives without proper backups.
Hardware failure
- such as hard drive crashes and power surges, can cause data loss due to age, manufacturing defects, or physical damage.
Software corruption
- that can lead to operating system failures and application errors, causing data loss or corruption, especially if the application was saving or processing data at the time.
Ransomware
- that encrypts data, demanding ransom for release, causing loss if backups are unavailable. Malicious software can corrupt data or cause systems to malfunction.
Stolen devices
- can cause permanent data loss if not backed up or encrypted, while misplacement can result in the permanent loss of data on USB drives or external hard drives.
Natural Disasters
- like earthquakes, floods, and fires can cause data loss due to their ability to destroy physical data storage locations without off-site backups.
Outdated technology
- such as outdated storage media like floppy disks or tape drives, can hinder data recovery due to degradation or lack of compatible hardware.
Outdated technology
- such as outdated storage media like floppy disks or tape drives, can hinder data recovery due to degradation or lack of compatible hardware.
Improper backups
- can result in significant data loss if primary data source fails, and improperly maintained or verified backups can become corrupted, making recovery impossible.
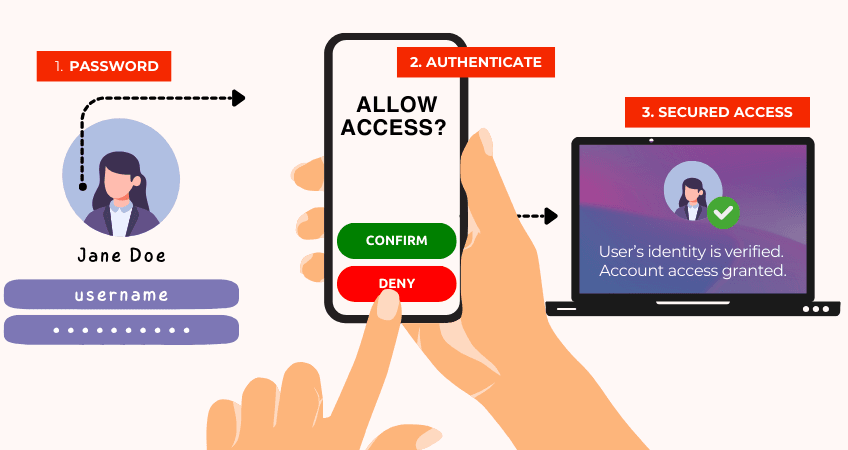
Make sure MFA is enabled.
This is a security minimum!
What are the types of MFA?
Knowledge (Something You Know)
Knowledge-based factors, such as passwords and PINs, and security questions, involve answering personal information like a mother's maiden name or a pet's name.
Possession (Something You Have)
Possession-based factors include one-time codes, authentication apps, physical devices, and chip-based cards for user authentication, which require physical reading and reader interaction.
Inherence (Something You Are)
Biometric authentication that may involve fingerprint scanning, facial recognition, iris scanning, and voice recognition.
Location (Somewhere You Are)
Location-based factors involve verifying a user's location using GPS coordinates and ensuring their login attempt is from a recognized or trusted IP address.
Why do you need Multi-factor Authentication (MFA)?
It significantly strengthens security by mitigating password vulnerabilities and protecting against common attacks. It ensures compliance with regulations like GDPR, HIPAA, and PCI-DSS standards. MFA safeguards sensitive information, reduces identity theft risk, and enhances user trust and confidence. It also mitigates insider threats by requiring two forms of access to sensitive systems. MFA solutions are user-friendly and easily integrated into existing systems, ensuring minimal disruption to user experience.

To prepare:
- Before upgrading to Windows 11, ensure your devices meet the specific hardware requirements, such as TPM 2.0 and newer processors.
- Develop a migration plan for businesses with multiple devices, ensuring upgrading to Windows 11 or transitioning to an alternative OS before the 2025 deadline.
- Prior to any transitions, it is crucial to ensure that all crucial data is securely backed up to prevent any potential loss during the upgrade process.