Robust IT infrastructure ensures heightened cybersecurity, safeguarding sensitive information from cyber threats. As businesses continue to navigate the digital age, those that prioritize and invest in IT are better positioned to adapt, thrive, and stay ahead of the competition.
Are you using the right technology to be effective and efficient? Spend 30 minutes with TechOnsite to review your technology stack.
The Need To Encrypt Your Business Email
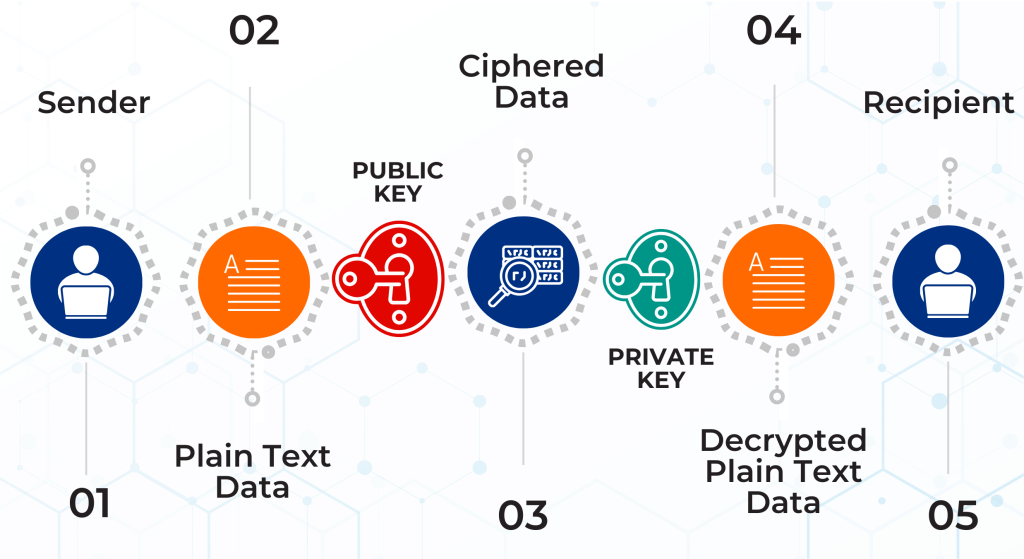
How Does Email Encryption Work?
Encryption Process
Public & Private Keys
Recipient's Public Key
Decryption
End-To-End Encryption
In summary, email encryption is a fundamental tool for protecting sensitive information, ensuring privacy, complying with regulations, and maintaining trust in digital communication. Whether for personal or business use, it’s an essential practice in our increasingly interconnected and data-driven world.

Note: MFA (Multi-factor authentication: at least two or more authentication methods) and 2FA (2-factor authentication: two methods of authentication)
- UNPREDICTABLE AND UNIQUE
Avoid easily guessable or commonly used passwords. Steer clear of examples like “password123” or birthdates. - VARIETY IS KEY
Employ a variety of characters, including uppercase and lowercase letters, numbers, and symbols. - REGULAR UPDATES
Change passwords at regular intervals to enhance security. - AVOID DICTIONARY WORDS
Refrain from using recognizable dictionary words, as these can be easily cracked using brute force attacks.
- TEXT MESSAGE CODES
Verification code to a registered phone number. - AUTHENTICATION APP GENERATED CODES
Time-sensitive codes generated within authentication apps. - BIOMETRICS
Biological markers like fingerprints. - PHYSICAL AUTHENTICATION CARDS
Smart cards with embedded chips.
Password Managers
Guarding Against Social Engineering
The Importance of MFA
The hackers’ intent was only to take over his Twitter account. If MFA had been in place, they would not have made progress, illustrating the critical role MFA plays in protecting our digital identities.

Copyright: Robyn Kessler Photography

Task Manager and Activity Monitor are system utility tools used to monitor and manage running processes and system resources on Windows and macOS, respectively. These tools are invaluable for troubleshooting performance issues and gaining insight into the health of your computer.
Task Manager in Windows provides a comprehensive view of all running processes, applications, and services. It displays essential information such as CPU and memory usage, disk activity, and network activity for each process. Users can easily identify resource-hungry applications or processes that may be causing system slowdowns or freezes. Task Manager also allows users to terminate unresponsive applications or processes, which can help resolve system issues without needing a full system restart. Additionally, it provides details about system startup programs and their impact on boot times.
Task Manager and Activity Monitor are essential tools for monitoring and managing system resources and processes on Windows and macOS systems. They provide detailed insights into resource usage, facilitate troubleshooting, and allow users to maintain optimal system performance. Whether a casual user or an IT professional, these utilities are indispensable for running your computer smoothly.
The Impact of Windows TPM
While Trusted Platform Modules (TPM) aren’t new, they’ve recently been given a spotlight due to their intensive requirement in Microsoft Windows 11.
There are distinct types of TPM implementations that one can use. Some are physically attached to the motherboard, some are built into the CPU through firmware, and some can be software-based (which isn’t recommended due to security risks). TPMs are intended to keep encryption keys, passwords, and other delicate information behind a wall so that malicious programs and attackers can’t easily use or edit that information.
In the past, Microsoft didn’t force its users or partners to turn TPM on for Windows to function properly, until Windows 11 was released and left many devices unable to install or upgrade to the Operating System. The situation worsened when Microsoft provided varied and contradictory information regarding its TPM requirements, resulting in further confusion from businesses and customers alike. Despite this, Microsoft did have valid concerns to address in requiring TPM. Over the years, malware attacks have become more frequent and persistent, with no signs of slowing down. Given Windows’ large user base, Microsoft has a lot to lose through lack of security on their Operating system.
While TPM was more widely used in business environments, Microsoft wants that kind of increased security to all its user base, even if it’s not a completely foolproof technology. The TPM is also responsible for encrypting drives (using Bitlocker) and Biometrics to sign in without a password (using Windows Hello), among other features. While TPMs will be able to assist with some specific attacks, it will be a mix of security procedures and sufficiently capable hardware that will keep businesses and customers safe.





